PRACTICAL EXAMPLES WITH FRIDA
Frida VS Anti-Debug Techniques on Windows (I)
February 4, 2021
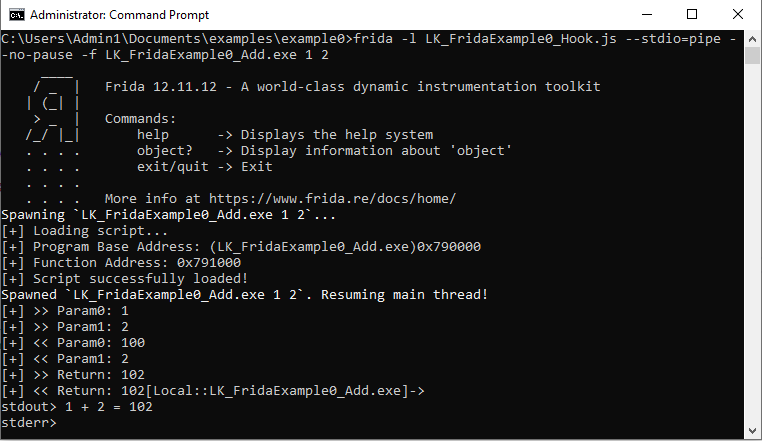
In this series of entries we are going to show practical examples of how to use Frida to bypass anti-debug techniques that some applications implement. This series begins with a short description of what Frida is, presenting the environment we will use for the examples we show later; followed…